Main Page
Welcome to the ETI (Encrypted Traffic Integration) Wiki
|
About ETSI's ETI TB
|
ETI Development Activity:
|
FAQ:
|
The ETI problem and why it needs solving
The role of encryption of information being transported between two end-points has three widely recognized positive purposes depending on the context:
- confidentiality protection of the transferred content;
- enhanced trust in the identity of the parties associated with the information; and
- enhanced trust in the integrity of the information during transport.
However, encryption may have a negative impact on third parties who do not have access to the encryption keys used and therefore do not have access to the content, but may have operational or legal responsibilities that require or are dependent on some level of knowledge of the information transported. Critical factors include how the keys were generated, who has knowledge of them, and how are they protected or shared.
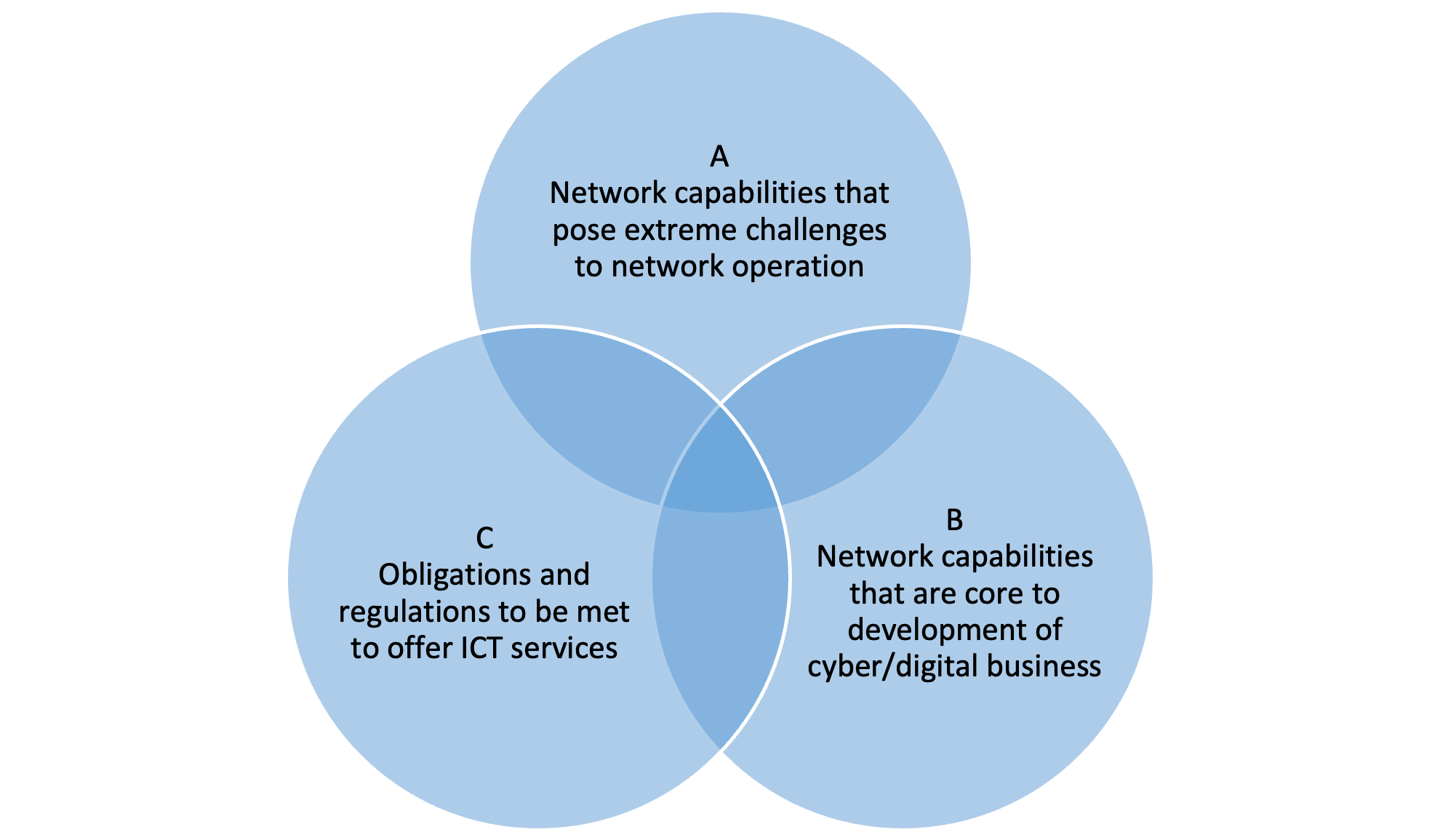
The ETI problem has looked at the Going Dark phenonom in which there is a concern that the inability of a normally authorized party such as the network management entity to function because of the encryption by end-point users or third parties. For example, the intersection of the two elements, A, representing network capabilities that, when content and headers are encrypted, pose extreme challenges to network operation, and B, representing Network capabilities that are core to the development of cyber/digital business, should be minimized, whilst always seeking to eliminate A, and further complicated by ensuring that the obligations placed on operators and suppliers with respect to regulation, law or convention, or operator security policy, are fulfilled (element C in the figure). The result is that whilst maximising the benefit of encryption as above it is also essential to maximise the viability of the service, and the ability to meet obligations set by 3rd parties.
The ETI problem is therefore centred on the more existential threat of pervasive encryption. What this means is that networks can only ever achieve best effort as all the meta data they require (in signalling mainly) is not available to them to make routing decisions, or assist in the minimisation of delay and jitter. It also means losing the ability to protect users from unsolicited content, and that introduces concerns about liability in failing to protect users.
The ETI ecosystem
This part of the WiKi is a translation and reformatting of the ETSI ISG ETI report on the eco-system as it applies to the work area of the group. In this respect the WiKi is intended as a living reference document for undertaking the responsibilities, areas of activity, organization and working methods enumerated in the Terms of Reference for Encrypted Traffic Integration. ETI is inherently diverse, dynamic, and spread across a complex array of bodies and activities worldwide, and constitutes a specialized ecosystem. The Group's effectiveness is predicated in large measure by constantly discovering, analysing, and understanding the diverse requirements and work occurring in this ecosystem in some kind of structured fashion. The present document should also be useful to the many constituents that are part of the encrypted traffic integration ecosystem.
A broad summary of the problem and why there is a requirement to develop mitigations is given in the ETI Problem Statement.
Therefore the primary purpose of this WiKi is to capture, discover, and assemble enumerated lists in alphabetic order of global encrypted traffic integration constituents. It attempts to be as inclusive as possible to expand collective insight into the extent and diversity of the ecosystem:
As far as is possible the material in this WiKi is collated in pages based on the above list. These can be navigated in conventional WiKi style by clicking on the links.
In addition this WiKi includes an extensive list of Terms and definitions, Abbreviations and some illustrative use cases of the relationships among the different groups.
This ecosystem changes constantly, so URIs provide links to the activities for the latest information.
Summary of recent updates
Quite a lot of the pages have had their placeholder lorem ipsum text replaced although there is still a lot remaining. As we increase the number of contributors this will change significantly. The most signficant changes recently are the pages and text surrounding Zero Trust and in particular the ZT-Kipling method that we are developing.
For a summary of the new publications in the field that we want to bring attention to we are citing certain Google Scholar results (other search engines will provide similar results).
The message here is that there is a lot of activity in the field and not all of it supportive of the wider aims of ETI.